False Flags and Forged E-mails
by Alphaville Herald on 05/09/13 at 4:58 pm
by Urizenus Sklar and Sara Jafary (Associate Editor, Herald Psyops Desk)
Over the past several years, Hacktivists like the members of Anonymous and leakers like Chelsea Manning, with the assistance of publishers like WikiLeaks, have exposed gigabytes of secrets of the American empire. The consequences have been far-reaching, and by some accounts the revelations helped fuel the Tunisian uprising and the subsequent Arab Spring.
One potential danger with any alleged hack or leak is that one wants to make sure it is legitimate. The original concept of WikiLeaks, after all, was that the vetting of alleged leaks could be crowdsourced. While WikiLeaks has since employed alternative ways of vetting documents, vetting by crowd sourcing is certainly a good idea and one that we should endorse. Leaks cannot be taken as automatically true and we cannot rely on government institutions or corporations for the truth on these matters. Leaks and the products of hacks need to be vetted by the hacktivist community. A recent hack provides an example of what is at stake and how we can crowdsource the vetting of important leaks and hacks.
Back on January 22, a hacker by the name of JAsIrX announced the release of documents from the hack of a private military contractor called Britam Defence. Critical emails among the documents suggested that the Qatari government and Britam were, with the blessing of the United States Government, discussing details of a false flag operation that would involve making a chemical weapon attack look like it was under Assad's control.
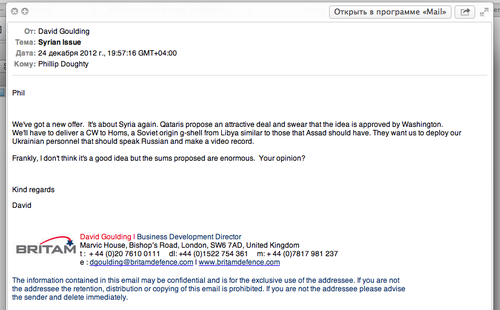
The Britam hack involved the release of gigabytes of information, but the principle smoking gun in the document dump was a Dec. 24 email apparently from Britam Defence's Business Development Director David Goulding to Founder and Dynamic Director of the firm Phillip Doughty (a former SAS officer):
Phil
We've got a new offer. It's about Syria again. Qataris propose an attractive deal and swear that the idea is approved by Washington.
We'll have to deliver a CW to Homs, a Soviet origin g-shell from Libya similar to those that Assad should have.
They want us to deploy our Ukrainian personnel that should speak Russian and make a video record.
Frankly, I don't think it's a good idea but the sums proposed are enormous. Your opinion?Kind regards David
false flag forgery?
CW, is of course shorthand for "chemical weapon," and a g-shell is a "gas shell" for delivering chemical weapons.The document dump also included a number of contracts, and information on employees, including a folder /Iraq/People/ that contained the photocopies of passports of several Ukrainians - presumably who would be drawn on for the operation.
Many of us read of the Britam hack back in January and didn't pay much attention to the contents at the time, but given recent events and the accompanying drumbeat to war, people are revisiting the released documents, which seem remarkably prescient. If the documents from that hack are authentic, they provide evidence that the United States gave its blessing to the Qataris for a false flag chemical warfare attack, presumably as a pretext to propel us into military intervention in Syria.
News of the Britam hack was originally published in the Daily Mail's online publication The Mail Online and in Cyber War News, which is a usually reliable online publication that keeps track of hacktivist actions - in particular those by Anonymous. This was soon followed by a counternarrative in which it was claimed that Britam had in fact been hacked, but that it was a state-sponsored hack - either by an Iranian groups or by the Syrian Electronic Army - and that the incriminating emails were faked. The Israeli online publication Ynet, summarized the counter-narrative as follows.
Computer security experts called in by Britam have proved that the emails relating to Syria and Iran were fabricated, the report said.
"They are 100% false," said Simon Lalor, Britam's chief executive. "From a technical point of view, the emails are fabricated. Who wrote the content is another question."
He estimated that the company had been "used as a vehicle to create tension and embarrassment for those with a political motivation."
The hacking is being investigated by cybercrime and counterterrorism specialists at Scotland Yard, likely in collaboration with the security services. Iran's possible involvement in the cyber attack is also being probed.
Britam subsequently sued the Daily Mail, which removed the story from its website (the story is still available via web archive) and apologized saying "the emails turned out to be forged". Other publications did not remove the story (a spokesperson for Cyber War News told us the breach of Britam had been authenticated even if individual documents had not, so they do not intend to remove the story).
With the recent developments in Syria the Brtiam false flag story has regained legs, and a number of online news sources have been suggesting that the emails are credible evidence of a false flag operation. These include voltairenet.org, beforeitsnews.com, globalresearch.ca, and rumormillnews.com. Meanwhile, The Examiner, which published the story when it first came out continues to keep the story online and that story has been linked to frequently on Facebook and elsewhere in social media.So what are we to make of this? Are all these documents the product of the Britam hack (which no one disputes having happened), or are some of them manufactured? If there is "proof" that the documents are fraudulent, it would be nice to know what that proof is.
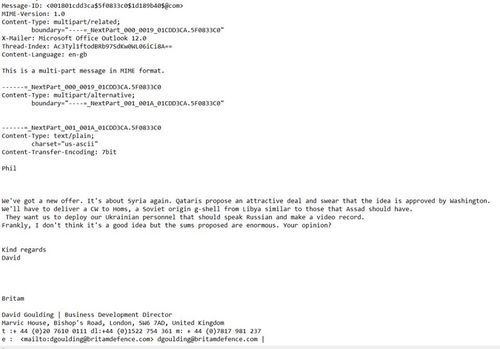
We asked some hacktivists connected with Anonymous to look into the matter and here is there basic assessment. While many of the files look legitimate, the document dump also included two emails (one on the Syrian false flag plot) that seem out of place in the context. The two emails in question are entitled "Iranian Issue" and "Syrian Issue". The real problem comes in the headers of the two emails.
Header from "Iranian Issue"
For; Thu, 16 Oct 2012 23:57:18 +0800 (SGT)
Received: (qmail 18137 invoked from network), 16 Oct 2012 15:57:27 -0000
Header from "Sirian Issue" [sic]
For; Mon, 24 Dec 2012 23:57:18 +0800 (SGT)
Received: (qmail 18137 invoked from network), 24 Dec 2012 15:57:27 -0000
is something odd in the e-mail header?
First, the process ID of the Qmail email program is the same (18137) and the possibility of two emails sent at different times having the same process ID is miniscule.
Second, the time on the emails is also identical down to the second. So it appears that the headers were the same and the hacker substituted two different messages in the body of the text. The only difference is the date. One is changed to 16 Oct and the other is set to 24 Dec. One problem with just changing the date is that the hacker forgot to change the day, so that it reads "Thu, 16 Oct 2012." Oct. 16, 2012 was a Tuesday. This is a devastating critique of the key letters that provided the evidence for a false flag operation.
None of this is to suggest that the Syrian gassing incident was not a false flag operation. Indeed The Mint Press has a very interesting article suggesting that Saudis provided the weapons to the rebels and that the attack was carried out by rebels (or perhaps the weapons were misused by the rebels).
It is also worth considering that the Britam hack might have been engineered by Britam itself and designed specifically to discredit anyone who might make a false flag charge. On the one hand, whoever made the forgery appears to have had access to an email that arrived on the Britam servers. Whoever made the forgeries was also clever enough to integrate some information on the emails with those of the legitimate material in the files - for example introducing an IP address from Singapore. But at the same time the forger made a very detectable error of getting the day of week wrong. So one might think that it could be an attempt to create an easily discredited false flag claim, thus inoculating Britam against future charges of that nature.
False flag operations are not new or rare. There is a long history of them, dating to the Roman Emperor Nero who used the pretext of the burning of Rome to carry out his persecution of Christians, and of course the burning of the Reichstag, which Adolf Hitler used as a pretext to purge the Communists from the German government.
False flag operations are also carried out by the United States - for example operation Ajax, which was an operation that removed Prime Minister Mohammed Mossadegh from power in Iran in 1953. According to declassified CIA records (detailed by James Risen of the New York Times), among the many other actions in that operation, Iranians working for the CIA posed as communists and harassed Iran's religious leaders, and in one case bombed the home of a leading cleric. The operation successfully turned the religious leadership against the Mossadegh government.
Today false flag operations are so salient in our culture that even video games like Modern Warfare include false flag elements. The problem with trying to expose a false flag operation today is that the Internet is clogged with people claiming that any tragedy or attack is some sort of false flag operation - a notable example being 9-11 truthers. Truthers and other conspiracy theorists thus end up being "useful idiots" for the power structure, as they undermine the credibility of actual conspiracies and false flag operations when they do arise.
And this is the problem. People claiming the possibility of a false flag operation in Syria needs to be particularly cautious to make sure that their evidence is in order. The credibility of the hacktivist movement demands that we get the facts right. We expect governments to lie when expedient. We expect corporations to lie when expedient. Hacktivists cannot afford to be casual with the truth. Getting at the truth is their fundamental cause. It cannot take a back seat to any other cause. Truth first.






Bubblesort
Sep 6th, 2013
Wasn’t there something in the Stratfor hack that said basically the same thing… that DC was shopping for a PMC to carry out a WMD attack in Syria to blame on Assad? Is that more reliable than the Britam hack?
Urizenus Sklar
Sep 6th, 2013
Bubblesort, I’ve seen plenty on Syria in the online Stratfor stuff but if there is something there on a false flag WMD attack I haven’t seen it.