Emerald Site Security Broken! Data Mining Shocks Linden Lab!!!
by Pixeleen Mistral on 11/05/10 at 4:40 am
According to documents that appear to have been leaked from ModularSystems, the developers of the “Emerald” Second Life viewer have compiled a database of avatar names, IP addresses, and geo-location information for players who created Second Life accounts at the ModularSystems.com site. In addition, visitors to the developers’ land in the virtual world have been profiled in the database.
The leaked documents include e-mail exchanges, a partial dump of the secret database, php source code for portions of a “datamine” application, and a picture of the Emerald developers in a meeting with Linden Lab CEO M Linden, Linden legal council Marty Linden, and several other Second Life staff.

Emerald meeting M Linden, Marty Linden, Joe Linden, and others (click image for closeup view)
Unfortunately, pictures of a virtual meeting with top Linden leadership may not reassure the virtual world’s rank and file residents, as they consider the implications of leaked documents appearing on anonymous file sharing sites.
There is a strong sexual role play component to the Second Life game, and many players are sensitive to linkage of real life information and game accounts, particularly in the hands of third parties who may be less circumspect than Linden Lab. Several of the Emerald developers have “colorful” reputations which may also raise some eyebrows.
Is a database connecting avatars and IP addresses of concern? According to an e-mail exchange with second life resident Hazim Grazov [full text below], Linden Lab staff seemed to think so. Soft Linden said, “I’m working with a VP on how to best deal with this. This is extremely serious”.
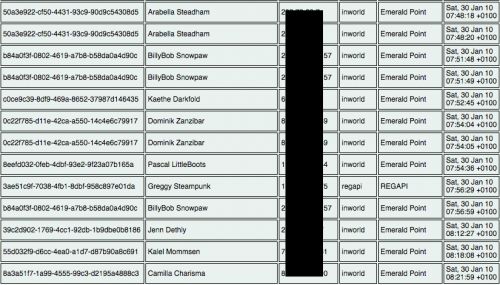
avatar keys, names, and IP addresses collected both in-world and via RegAPI
Soft Linden’s concerns are echoed in an e-mail dated April 16th, in which Joe Linden tells Mr. Grazov, “We consider this a very serious event and have not finished our discussions with them as to next steps, privacy policy modifications, and communications with their users. I don’t know what the source of the file was, but if you know, I hope you will encourage them not to release it publicly.” Joe concludes by saying, “Thanks again for making us aware of this. Rest assured, we do not treat events like this lightly”.
However, it is unclear how seriously Linden Lab is treating the situation. This morning, the Herald contacted both Soft Linden and Joe Linden for comment. As we go to press 12 hours later, neither have replied and it is unknown what – if any – steps have been taken to limit the data collection.
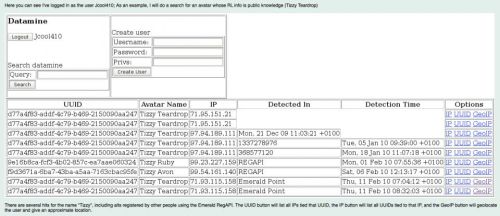
Jcool410 searches for Tizzy
According to the leaked documents, several Emerald developers were able to run searches against the database. One document shows a user named Jcool410 performing a “datamine” search – but it appears that Jcool410 ‘s account had been compromised. Other documents list what are believed to be Jcool410’s passwords — apparently Jcool did not get the memo warning against using passwords found in the dictionary.

Welcome to Burbank!
Asked via Skype Saturday if there had been a breach of security at the modularsystems.com site, Jcool – who is known as Fractured Crystal in Second Life – declined to comment.
While it is possible that some of the documents have been fabricated, I can confirm at least two e-mail messages found in the Emerald Revealed documents are legitimate — both are chat messages that I sent to Fractured Crystal while he was offline and which were automatically forwarded to e-mail.
The news that Hazim Grazov raised questions about the Emerald developers’ data mining operation with Joe and Soft Linden will certainly lead to speculation that the recent Woodbury University Second Life ban was connected to the Emerald leaks. Mr. Grazov is known to have spent time with members of the Woodbury group in Second Life, and there was a confrontation between some members of the Woodbury faction and Fractured Crystal (a.k.a. Jcool410) shortly before Linden Lab removed the Soviet Woodbury sims and their leadership from the game.
As the Herald staff sifts through the Emerald Revealed documents, I am struck by the similarities between this confrontation and that of the Nicholas / Sephora mafia wars — the gameplay leaks out into the real world and website security breaches are used to score points against the other faction.
But are both sides treating this as just another game?
————————————————————————————–
Subject: Re: Someone told me you might want to see this RE Emerald…
Date: Fri, 16 Apr 2010 14:05:22 -0700
From: Joe Linden <joe@lindenlab.com>
To: Hazim Gazov <hazim.gazov@gmail.com>
Cc: Soft Linden <soft@lindenlab.com>
We consider this a very serious event and have not finished our discussions
with them as to next steps, privacy policy modifications, and communications
with their users.
I don’t know what the source of the file was, but if you know, I hope you
will encourage them not to release it publicly.
By the way, we determined that yours was the only voice account that had
been disabled. Is voice working for you again?
Thanks again for making us aware of this. Rest assured, we do not treat
events like this lightly.
Regards,
– Joe Miller
On Fri, Apr 16, 2010 at 1:36 PM, Hazim Gazov <hazim.gazov@gmail.com> wrote:
> I heard the explanation Jay gave as to why he had the info, and I don’t buy
> it.
>
> The database allowed administrators to quickly determine if a new account
>> was a alt account of a griefer that had previously attacked the sim. It also
>> stored the IP used on registration portal on the website when you register a
>> avatar because avatars created on that portal usually logged directly into
>> Emerald Point and were the fastest route for griefing the sim. After it was
>> demonstrated that this was a effective solution to the problem, several
>> nodes were placed in a few other sims for short periods of time
>>
>
> Since when do you need GeoIP functionality to determine if someone is an
> alt? From what I heard they had rather large GeoIP files used to obtain an
> approximate location from an IP address and had the code built into the
> system:
>
> From datemine.web.php:
>
>> $gi = geoip_open("geoip/GeoLiteCity.dat",GEOIP_STANDARD);
>> $giorg = geoip_open("geoip/GeoIPOrg.dat",GEOIP_STANDARD);
>> $giisp = geoip_open("geoip/GeoIPISP.dat",GEOIP_STANDARD);
>> $tip = $_GET['ip'];
>>
>> $record = geoip_record_by_addr($gi,$tip);
>>
>> /*$netspeed = geoip_country_id_by_addr($gi,$tip);
>> if ($netspeed == GEOIP_UNKNOWN_SPEED)$netspeed =
>> ‘Unknown’;
>> }else if ($netspeed == GEOIP_DIALUP_SPEED)$netspeed =
>> ‘Dailup’;
>> }else if ($netspeed == GEOIP_CABLEDSL_SPEED)$netspeed =
>> ‘Cable/DSL’;
>> }else if ($netspeed == GEOIP_CORPORATE_SPEED)$netspeed =
>> ‘Corporate’;
>> else $netspeed = ‘???’;*/
>>
>> $org = geoip_org_by_addr($giorg,$tip);
>> $isp = geoip_org_by_addr($giisp,$tip);
>>
>
> I sincerely hope something more than a slap on the wrist is doled out.
>
> I’ve also heard that my IP was sent as the person who "hacked" into their
> website, that’s bull and they should pony up some logs if they want to say
> that. I wouldn’t be surprised if they just pulled up the IP from that
> database.
>
> On Thu, Apr 15, 2010 at 11:32 PM, Hazim Gazov <hazim.gazov@gmail.com>wrote:
>
>> Unfortunately, I wasn’t the first one to get this, so I don’t think I can
>> do much to limit the sharing of it… however AFAIK very few people have one
>> with full IP addresses, most people have one with the last two blocks
>> censored.
>>
>>
>> On Thu, Apr 15, 2010 at 6:05 PM, Soft Linden <soft@lindenlab.com> wrote:
>>
>>> Yep, I see that, and I see the regapi collection. I’m working with a
>>> VP on how to best deal with this. This is extremely serious.
>>>
>>> Do you know how widely this has been spread, and could I trust you to
>>> limit further sharing?
>>>
>>> On Thu, Apr 15, 2010 at 12:25 PM, Hazim Gazov <hazim.gazov@gmail.com> wrote:
>>> > It’s being retained for the purpose of getting an SL user’s RL data
>>> > arbitrarily.
>>> >
>>> > On Thu, Apr 15, 2010 at 4:22 PM, Hazim Gazov <hazim.gazov@gmail.com> wrote:
>>> >>
>>> >> They’re not simply being retained, look at
>>> >> secondlifeutility/datamine.web.php
>>> >>
>>> >> On Thu, Apr 15, 2010 at 4:18 PM, Soft Linden <soft@lindenlab.com> wrote:
>>> >>>
>>> >>> I appreciate the heads up, Hazim, and I’m disappointed to see that the
>>> >>> IP addresses are being retained. I’ll let the appropriate Lindens
>>> >>> know.
>>> >>>
>>> >>> On Thu, Apr 15, 2010 at 11:57 AM, Hazim Gazov <hazim.gazov@gmail.com> wrote:
>>> >>> >
>>> >>> >
>>> >>> > ———- Forwarded message ———-
>>> >>> > From: Hazim Gazov <hazim.gazov@gmail.com>
>>> >>> > Date: Thu, Apr 15, 2010 at 3:50 PM
>>> >>> > Subject: Re: Someone told me you might want to see this RE Emerald…
>>> >>> > To: joe@lindenlab.com
>>> >>> >
>>> >>> >
>>> >>> > and I forgot the attachment, spectacular
>>> >>> >
>>> >>> > On Thu, Apr 15, 2010 at 3:49 PM, Hazim Gazov <hazim.gazov@gmail.com> wrote:
>>> >>> >>
>>> >>> >> Take a look at the SQL file and regapi/index.php at line 97…
>>> >>> >
>>> >>> >
>>> >>> >
>>> >>
>>> >
>>> >
>>>
>>
>>
>






Uncheck “Drama” in Preferences « Herding Cats
Aug 21st, 2010
[...] A catalog of IP addresses of Second Life users collected by Emerald developers was released, containing information allowing the connection of avatars to their alts. [...]
BEWARE: An Emerald in the Rough «
Aug 22nd, 2010
[...] recently regarding the popular Modular Systems Emerald Viewer, and it’s all bad. From the leaked avatar database to the ability to track avatar alts, to the brand new DDoS proof of concept that was unleased [...]
“La guerra dei viewer” Emerald rimosso dall’elenco dei viewer accettati « VIRTUAL WORLDS MAGAZINE
Aug 23rd, 2010
[...] ultimi mesi Emerald era incappato in diversi problemi relativi alla privacy, alla raccolta di dati privati, e la stessa reputazione di molti programmatori di Emerald era molto dubbia essendo stati coinvolti [...]
Anatomy of a scandal « Second Life Shrink
Aug 24th, 2010
[...] to really quantify the risks involved, producing a haze of uncertain anxiety. Then there was the Woodbury sub-plot, and the allegations of Linden collusion, which added another layer of conspiracy theories (all that was missing was the JLU). Perhaps most [...]
Serendipity Seraph
Aug 24th, 2010
So freaking what? What could you do knowing Serendipity Seraph has a ISP cable box with such and such IP? If you are lucky that gives you a rough physical address. If unlucky you get the Comcast local address. Then what? Nothing much. They can’t get my iRL name from it without ISP cooperation. Such cooperation to private parties would be a VERY BIG DEAL. If you play from a static IP that has DNS registration to your own iRL name that you didn’t bother to make private – then it could be tracked. Or if one had enough email poked around in their full headers to find any other corresponding names they might be able to do it. But there is no evidence offered that Emerald guys went to such lengths.
I have received not one shred of spam or anything else due to occasionally using Emerald or any other viewer.
May I point out that IP information is encoded in every single network packet that you send in any and every program whatsoever? May I point out that it is considered fair game on websites to log this stuff?
That Emerald bothered to make a database of it doesn’t bother me at all. It would bother me if they actually did anything malicious with it. But where is that proved?
Kristopher Quandry
Aug 26th, 2010
Good post. I added this info to my site if you don;t mind, crediting you as source. Everyone i know uses emerald viewer so they are all concerned and nervous.
I also am doing a PodCast regarding this issue with emerald, and have permission from Fractured Crystal to use his “explanation” blog post as my basis.
Thanks for the info re: Linden Labs. Very important we understand everything that is happening
Little Lost Linden
Aug 29th, 2010
@Serendipity.
Pretty simple through means of social engineering to obtain your rl creds from your ip address from an ISP.
http://www.symantec.com/connect/articles/social-engineering-fundamentals-part-i-hacker-tactics
Gundel Gaukelei
Aug 29th, 2010
“So freaking what? What could you do knowing Serendipity Seraph has a ISP cable box with such and such IP?”
If you want to find out, start messing with the wrong, err right people …
Was Vivox Chat p0wned by Emerald Developers? | The Alphaville Herald
Aug 30th, 2010
[...] wars between the Emeralds and the Soviet Woodbury group to new levels after the Emerald’s site security was compromised and the data mining operation was revealed. This weekend, a source we will refer to as DeepYiff has [...]
Fred Martian
Sep 3rd, 2010
With access to other databases with IP addresses and smart cross correlation you can quickly come up with very interesting data.
SL Population Crash Continues | The Alphaville Herald
Apr 11th, 2011
[...] visiting a surveillance-friendly virtual dystopia is an acquired taste, and not everyone wants to play stalk-and-ban-the-other-players, or hunt down [...]
GG3
Apr 25th, 2011
It’s a sad day when Second Life users call themselves “locking” others out of the grid by using malicious means. First Woodbury, now Red-Zone(which was a money-scam pit to began with). Linden Labs needs to get a hold of this and treat these IP sniffers with a penalty as serious as age-play.
In other words Zero-Tolerance.
These are users who have been on Second-Life well enough that their behavior is totally inexcusable and unacceptable. Using those who troll/”grief” fake sims is NOT a good excuse to invade people’s real-life privacy. Information like this freely thrown around by random idiots who call themselves “cleansing” the grid need a reality check and a swfit-ban hammer in the rear-end. The internet is the internet and things of those nature will occur. It cannot be stopped, it cannot be “controlled”.
Those so called “residents” of Second-Life who are using the service thinking they have a right to stalk/harass others are clearly wrong. That includes all groups who call themselves “policing” the service Second-Life.
“La guerra dei viewer” Emerald rimosso dall’elenco dei viewer accettati | VIRTUAL WORLDS MAGAZINE
Oct 18th, 2013
[...] ultimi mesi Emerald era incappato in diversi problemi relativi alla privacy, alla raccolta di dati privati, e la stessa reputazione di molti programmatori di Emerald era molto dubbia essendo stati coinvolti [...]
» Modular Systems Hacked
Nov 8th, 2013
[...] of the hacking operation was posted on May 11, 2010, on a Second Life-specific blog called “The AlphaVille Herald”, known for its heavily anarchist and anti-establishment bias. A very busy stream of comments [...]