Emerald Site Security Broken! Data Mining Shocks Linden Lab!!!
by Pixeleen Mistral on 11/05/10 at 4:40 am
According to documents that appear to have been leaked from ModularSystems, the developers of the “Emerald” Second Life viewer have compiled a database of avatar names, IP addresses, and geo-location information for players who created Second Life accounts at the ModularSystems.com site. In addition, visitors to the developers’ land in the virtual world have been profiled in the database.
The leaked documents include e-mail exchanges, a partial dump of the secret database, php source code for portions of a “datamine” application, and a picture of the Emerald developers in a meeting with Linden Lab CEO M Linden, Linden legal council Marty Linden, and several other Second Life staff.

Emerald meeting M Linden, Marty Linden, Joe Linden, and others (click image for closeup view)
Unfortunately, pictures of a virtual meeting with top Linden leadership may not reassure the virtual world’s rank and file residents, as they consider the implications of leaked documents appearing on anonymous file sharing sites.
There is a strong sexual role play component to the Second Life game, and many players are sensitive to linkage of real life information and game accounts, particularly in the hands of third parties who may be less circumspect than Linden Lab. Several of the Emerald developers have “colorful” reputations which may also raise some eyebrows.
Is a database connecting avatars and IP addresses of concern? According to an e-mail exchange with second life resident Hazim Grazov [full text below], Linden Lab staff seemed to think so. Soft Linden said, “I’m working with a VP on how to best deal with this. This is extremely serious”.
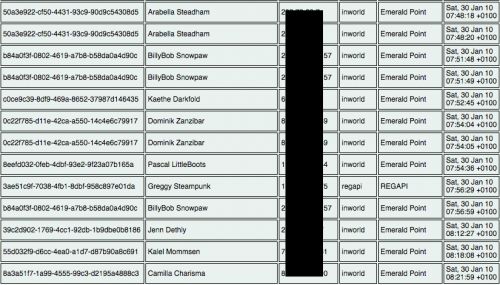
avatar keys, names, and IP addresses collected both in-world and via RegAPI
Soft Linden’s concerns are echoed in an e-mail dated April 16th, in which Joe Linden tells Mr. Grazov, “We consider this a very serious event and have not finished our discussions with them as to next steps, privacy policy modifications, and communications with their users. I don’t know what the source of the file was, but if you know, I hope you will encourage them not to release it publicly.” Joe concludes by saying, “Thanks again for making us aware of this. Rest assured, we do not treat events like this lightly”.
However, it is unclear how seriously Linden Lab is treating the situation. This morning, the Herald contacted both Soft Linden and Joe Linden for comment. As we go to press 12 hours later, neither have replied and it is unknown what – if any – steps have been taken to limit the data collection.
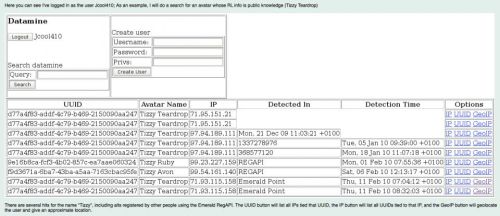
Jcool410 searches for Tizzy
According to the leaked documents, several Emerald developers were able to run searches against the database. One document shows a user named Jcool410 performing a “datamine” search – but it appears that Jcool410 ‘s account had been compromised. Other documents list what are believed to be Jcool410’s passwords — apparently Jcool did not get the memo warning against using passwords found in the dictionary.

Welcome to Burbank!
Asked via Skype Saturday if there had been a breach of security at the modularsystems.com site, Jcool – who is known as Fractured Crystal in Second Life – declined to comment.
While it is possible that some of the documents have been fabricated, I can confirm at least two e-mail messages found in the Emerald Revealed documents are legitimate — both are chat messages that I sent to Fractured Crystal while he was offline and which were automatically forwarded to e-mail.
The news that Hazim Grazov raised questions about the Emerald developers’ data mining operation with Joe and Soft Linden will certainly lead to speculation that the recent Woodbury University Second Life ban was connected to the Emerald leaks. Mr. Grazov is known to have spent time with members of the Woodbury group in Second Life, and there was a confrontation between some members of the Woodbury faction and Fractured Crystal (a.k.a. Jcool410) shortly before Linden Lab removed the Soviet Woodbury sims and their leadership from the game.
As the Herald staff sifts through the Emerald Revealed documents, I am struck by the similarities between this confrontation and that of the Nicholas / Sephora mafia wars — the gameplay leaks out into the real world and website security breaches are used to score points against the other faction.
But are both sides treating this as just another game?
————————————————————————————–
Subject: Re: Someone told me you might want to see this RE Emerald…
Date: Fri, 16 Apr 2010 14:05:22 -0700
From: Joe Linden <joe@lindenlab.com>
To: Hazim Gazov <hazim.gazov@gmail.com>
Cc: Soft Linden <soft@lindenlab.com>
We consider this a very serious event and have not finished our discussions
with them as to next steps, privacy policy modifications, and communications
with their users.
I don’t know what the source of the file was, but if you know, I hope you
will encourage them not to release it publicly.
By the way, we determined that yours was the only voice account that had
been disabled. Is voice working for you again?
Thanks again for making us aware of this. Rest assured, we do not treat
events like this lightly.
Regards,
– Joe Miller
On Fri, Apr 16, 2010 at 1:36 PM, Hazim Gazov <hazim.gazov@gmail.com> wrote:
> I heard the explanation Jay gave as to why he had the info, and I don’t buy
> it.
>
> The database allowed administrators to quickly determine if a new account
>> was a alt account of a griefer that had previously attacked the sim. It also
>> stored the IP used on registration portal on the website when you register a
>> avatar because avatars created on that portal usually logged directly into
>> Emerald Point and were the fastest route for griefing the sim. After it was
>> demonstrated that this was a effective solution to the problem, several
>> nodes were placed in a few other sims for short periods of time
>>
>
> Since when do you need GeoIP functionality to determine if someone is an
> alt? From what I heard they had rather large GeoIP files used to obtain an
> approximate location from an IP address and had the code built into the
> system:
>
> From datemine.web.php:
>
>> $gi = geoip_open("geoip/GeoLiteCity.dat",GEOIP_STANDARD);
>> $giorg = geoip_open("geoip/GeoIPOrg.dat",GEOIP_STANDARD);
>> $giisp = geoip_open("geoip/GeoIPISP.dat",GEOIP_STANDARD);
>> $tip = $_GET['ip'];
>>
>> $record = geoip_record_by_addr($gi,$tip);
>>
>> /*$netspeed = geoip_country_id_by_addr($gi,$tip);
>> if ($netspeed == GEOIP_UNKNOWN_SPEED)$netspeed =
>> ‘Unknown’;
>> }else if ($netspeed == GEOIP_DIALUP_SPEED)$netspeed =
>> ‘Dailup’;
>> }else if ($netspeed == GEOIP_CABLEDSL_SPEED)$netspeed =
>> ‘Cable/DSL’;
>> }else if ($netspeed == GEOIP_CORPORATE_SPEED)$netspeed =
>> ‘Corporate’;
>> else $netspeed = ‘???’;*/
>>
>> $org = geoip_org_by_addr($giorg,$tip);
>> $isp = geoip_org_by_addr($giisp,$tip);
>>
>
> I sincerely hope something more than a slap on the wrist is doled out.
>
> I’ve also heard that my IP was sent as the person who "hacked" into their
> website, that’s bull and they should pony up some logs if they want to say
> that. I wouldn’t be surprised if they just pulled up the IP from that
> database.
>
> On Thu, Apr 15, 2010 at 11:32 PM, Hazim Gazov <hazim.gazov@gmail.com>wrote:
>
>> Unfortunately, I wasn’t the first one to get this, so I don’t think I can
>> do much to limit the sharing of it… however AFAIK very few people have one
>> with full IP addresses, most people have one with the last two blocks
>> censored.
>>
>>
>> On Thu, Apr 15, 2010 at 6:05 PM, Soft Linden <soft@lindenlab.com> wrote:
>>
>>> Yep, I see that, and I see the regapi collection. I’m working with a
>>> VP on how to best deal with this. This is extremely serious.
>>>
>>> Do you know how widely this has been spread, and could I trust you to
>>> limit further sharing?
>>>
>>> On Thu, Apr 15, 2010 at 12:25 PM, Hazim Gazov <hazim.gazov@gmail.com> wrote:
>>> > It’s being retained for the purpose of getting an SL user’s RL data
>>> > arbitrarily.
>>> >
>>> > On Thu, Apr 15, 2010 at 4:22 PM, Hazim Gazov <hazim.gazov@gmail.com> wrote:
>>> >>
>>> >> They’re not simply being retained, look at
>>> >> secondlifeutility/datamine.web.php
>>> >>
>>> >> On Thu, Apr 15, 2010 at 4:18 PM, Soft Linden <soft@lindenlab.com> wrote:
>>> >>>
>>> >>> I appreciate the heads up, Hazim, and I’m disappointed to see that the
>>> >>> IP addresses are being retained. I’ll let the appropriate Lindens
>>> >>> know.
>>> >>>
>>> >>> On Thu, Apr 15, 2010 at 11:57 AM, Hazim Gazov <hazim.gazov@gmail.com> wrote:
>>> >>> >
>>> >>> >
>>> >>> > ———- Forwarded message ———-
>>> >>> > From: Hazim Gazov <hazim.gazov@gmail.com>
>>> >>> > Date: Thu, Apr 15, 2010 at 3:50 PM
>>> >>> > Subject: Re: Someone told me you might want to see this RE Emerald…
>>> >>> > To: joe@lindenlab.com
>>> >>> >
>>> >>> >
>>> >>> > and I forgot the attachment, spectacular
>>> >>> >
>>> >>> > On Thu, Apr 15, 2010 at 3:49 PM, Hazim Gazov <hazim.gazov@gmail.com> wrote:
>>> >>> >>
>>> >>> >> Take a look at the SQL file and regapi/index.php at line 97…
>>> >>> >
>>> >>> >
>>> >>> >
>>> >>
>>> >
>>> >
>>>
>>
>>
>






Deadlycodec
May 13th, 2010
IP Addresses are not private. You don’t even own your IP. Your ISP does. THEY are registered with the Internet Assigned Numbers Authority, not the home user. You just lease it from them for a monthly rate, and literally ANY computer that you visit (including this one, where you’re reading this) stores that information in access logs and/or error logs for debugging, and also for security purposes. Unless you’re running a webserver on that IP address or something, there isn’t much anyone can do with it except maybe determine the city in which you live.
When your computer (or router) is connected to the internet, it usually obtains an IP address using Dynamic Host Configuration Protocol. For the average person, this isn’t even a static ip. It’s leased, and every few months or so may change. It will also change if you change your mac address (if you aren’t behind a LAN) and power cycle your cable modem.
My point is that none of this is really relevant to your privacy at all. What, do you think some hacker is randomly going to haxzor your IP? Unless you’re lacking firewalls and running a ton of service and/or a webserver then this is very unlikely (as in most cases) and an attacker would be far more likely to target you using social engineering with XSS, CRLF, and other various techniques that are more likely to succeed.
V
May 13th, 2010
I suggest we all stop feeding trolls now.
Gaara Sandalwood
May 13th, 2010
om nom nom nom nom.
Kiddoh
May 13th, 2010
I like how a lot of people are missing the point entirely, either because they can’t comprehend it or they’re stopping at the first contradiction and totally ignoring the rest.
http://www.sluniverse.com/php/vb/general-sl-discussion/44270-oh-snap.html
Goto that link. It’s light-years ahead of the comments within the Herald Article.
K.T.D.
May 13th, 2010
@deadlycodec:
Your trash isn’t private either once you put it on the curb. I would still guess you wouldn’t appreciate it if you went out for a smoke and found some cunt rummaging through it for information or some dirt on your personal habits.
It’s a matter of respecting other people’s boundaries, something which the Emerald devs have shown they do not give half a shit about. Instead they choose to be a cunt about things, and when they get caught, they dismiss the issue because “Anyone can do it if they know how!”.
I could go around running my 50cc 2-stroke motored bike at WOT all the time if I wanted to as well, it’s road legal in this place, and there are no laws on the books regulating the exhaust note’s decibel level. That does not mean I should repeatedly ride it in front of other people’s houses at 7AM on a Sunday morning. It’s antisocial and inconsiderate.
Could my neighbors stop me from doing it? Not really, but you can bet that they would have some nasty comments for me if I did it.
V
May 13th, 2010
@Kiddoh: By now, I’m on page 8 of that thread and my brain feels like melting as it usually just does on /b/. So, please spare me further pain and tell me how or where this is light-years ahead. Unless by ‘light-years ahead’ you meant ‘spaced out’.
Kiddoh
May 13th, 2010
You have to read the whole damn thing. Although there’s some rather retarded posts in it, there are already counters and evidence and examples provided for every point that has been made within the Herald Comments and thus why I say it’s light-years ahead. I figure I would just save everyone the time and effort. \D
David McNaughten
May 13th, 2010
Better that than this – the Herald is just a mouthpiece for griefer groups now, so you can’t expect much in the way of actual information from it that isn’t heavily biased towards anarchy and hacking if the last six month’s articles are any indication. (What were the editors thinking backing Woodbury all this time?)
The Avatar Formally Known As . . .
May 13th, 2010
David, the herald is sooo pro MS right? anarchy and hacking . . .
At0m0 Beerbaum
May 14th, 2010
The only group that will be left in SL in the end will be the furfags.
this is further proof
Gaara Sandalwood
May 14th, 2010
Been there Kiddoh. Been keeping up with the whole thign, but it took me soem time to catch up. Props to Jesse btw.
At0m0 Beerbaum
May 14th, 2010
@ K. T. D.
“I could go around running my 50cc 2-stroke motored bike at WOT all the time if I wanted to as well, it’s road legal in this place, and there are no laws on the books regulating the exhaust note’s decibel level. That does not mean I should repeatedly ride it in front of other people’s houses at 7AM on a Sunday morning. It’s antisocial and inconsiderate.”
Haha you drive a moped.
Judge Joker
May 14th, 2010
@At0m0 Beerbaum
“Haha you drive a moped.”
Oh come on At0m0, can’t you make up something better for us to laugh at with you as opposed to at you? this ain’t the 4th grade.
“The only group that will be left in SL in the end will be the furfags.”
Even if that was true it would be further proof of one of the ageless laws of nature being acted out in the dramatic theater of Second Life, “survival of the fittest”, of course being able to survive by At0m0c banmute is no real sweat inducing workout.
Anon
May 14th, 2010
http://www.rapidspread.com/file.jsp?id=bhihdfznue
Onyx SVN Dump
dump emerald devs
May 14th, 2010
Thanks for that link Anon… not sure what it is but… if it compiles I guess we will see… (what it is)…
Yeah, this sneakthief datamining by emerald is way worse than anything that the PN or WU ever did. LL should boot every last one of them just like they did WU.
Hell, yesterday MarkTwain White toasted off the head of “Pirate Air” in the Blake Sea and his 724 members, just one day booted them all out of their Sim that they were renting, after a hallucenigenic internescene battle between the PA (kinda rhymes with PN) and about 6 other air squadrons who are in a cut throat competition for air dominance in the Blake sea. Google “outlaw acker” and look for the pastbin entry if you are interested in pulling a thread that speaks to just how brittle things are getting in SL.
Protect everyone and just shut it all down
Miss J
May 14th, 2010
LOL Onyx made its way on to torrents now. Good luck Emerald team.
yeah
May 14th, 2010
onyx spreading will be fun
無名氏
May 14th, 2010
Looking forward to the weekend then ¤_¤
Eggy Lippmann
May 14th, 2010
I’m sorry, did you seriously report on people having their IP logged with a modified viewer?
You know that I can log your IP if you simply fly over my land and access my mp3 stream, right?
And with a modified viewer out there trawling for popularity, I could have so much more fun than logging your IP!
I could get everybody’s passwords, then when critical mass was achieved, I would log everybody at once, sell their L$ for next to nothing, and crash the stock market, or simply give them to NULL_KEY and make all the money in this sorry excuse for a stock market disappear, or remote control your avatars with libopenmv and DoS someone, or what have you.
HELLO? EVERY WEB SERVER LOGS YOUR IP INCLUDING THIS ONE!
V
May 14th, 2010
Wow, Eggy, it’s good to finally see someone who really understands the issue. Where have you been all this time? We’ve been waiting for you.
Darien Caldwell
May 14th, 2010
Just because you *can* do something, doesn’t make it *right* to do so.
This is what so many youngsters seem unable to comprehend.
They can just as easily *not* store the IPs, as store them. They chose to store them. That was a bad decision. /thread
The Avatar Formally Known As . . .
May 14th, 2010
Another doche detracting from the real issue by palming the issue as ip address. Moron!
K.T.D.
May 14th, 2010
@At0m0:
Yeah, my Lexus is in the shop right now. How many street legal motorized vehicles have you built in the real world?
Hazim Gazov
May 14th, 2010
What the hell is a “doche”?
The Avatar Formally Known As . . .
May 14th, 2010
Its a douche without you. A typo really.
Kiddoh
May 14th, 2010
“Wow, Eggy, it’s good to finally see someone who really understands the issue. Where have you been all this time? We’ve been waiting for you.”
Unfortunately for both you and him, it seems the only thing you two can comprehend are IP addresses when there are multiple other issues that need to be discussed. \D
V
May 14th, 2010
\D
Kiddoh
May 14th, 2010
http://i40.tinypic.com/33m94zb.jpg
Hazim Gazov
May 14th, 2010
@Anon
Wait, someone actually dumped it from Ph0x’s other box? I lol.
But yeah, just quickly going over it it looks like that’s legit, but from October.
Dongs Lol
May 14th, 2010
http://www.rapidspread.com/file.jsp?id=yzypd16gmg
The dump was a rip of the Onyx SVN repository from the SVN server. here’s a proper archive of the Onyx source for your griffing pleasure.
Jayd3n
May 15th, 2010
Woot Yay Onyx, I will get these to my Debug Team right away, already have them downloaded, we will do some serious shiet with them to the emerald team (; I will also pass them out to everyone else who doesn’t have them and help re upload them.
IF Modular systems, and Onyx Team wants to play
BOYS WE HAVE A TRAITOR/ SPY WITH ME, and everyone else is up for it im in (;
Selkit Diller
May 15th, 2010
…Heh. I find it entertaining how worked up some of you are getting over a gently modified VLife client. I don’t think I’ll be able to hold back a chuckle or two if the person wanting to drop a thousand bucks actually did drop a thousand bucks on outdated code a disgruntled ex Emerald coder wandered off with sometime last year.
Skyler
May 15th, 2010
so, if i never made and account on modularsystems.com and never visited their land, can i still use emerald viewer?
makomk
May 15th, 2010
Anon: oh wow. There’s a feature in there intended to let you establish a trusted session with the server and become any user you want to be or give yourself admin. Presumably this has been fixed since then, but still.
Selkit Diller
May 15th, 2010
@Skyler;
Personally, I won’t use a precompiled binary of Emerald, but then, that’s simple good practice paranoia in action. If you want to use it, do the responsible thing, compile from source, and check the source yourself. Better yet? Check the checksum of the source you compile (after manual code review) against their provided binary. As for how… no offense, but if you aren’t aware, it’ll take me days I don’t feel like spending teaching you how.
Hazim Gazov
May 15th, 2010
Regardless of how funny some of you think it is that Onyx has been leaked and some people are building binaries to give out, I really wouldn’t run them if only for the fact that it’s severely outdated and would be easily picked up by LL (and anyone looking to exploit people using outdated viewers.)
ModularSystems=New G-team
May 15th, 2010
@Selkit.
As I said earlier, and I’m sure you’ve noticed the differences. The source is definately not what is used to make the binaries.
I also look through the updates for anything, odd looking.
@makomk
It probably isn’t fixed. Spoofing session IDs is probably how obtaining inventories are possible and God powers, i’e mapping, forcetping, etc.
ModularSystems=New G-team
May 16th, 2010
But either way, I think I’ll be parting with the Modular/Onyx/Jcool/Phox/LuminousLuminous flame threads now, rather pointless. Those who know the truth will take their own methods of using or not using Emerald or SL viewers and those who don’t will continue to boost the credentials of Modular by downloading those binaries with shiny prims and bouncy boobs.
Those who have the real power to do something(Soft, Oskar, the entire user base) will continue to stroke the cock of Modular while the G team cradles the balls. These threads are less informative than they are pointless venting, myself included.
Me and my friends are off to make some copybot viewers in different variations, than stop them and tell LL how to patch them and admit we were wrong and sorry, then harvest some IPs and User names, maybe copybot a few items here and there, anyone care to join?
I promise we’ll be the new G team in less than 2 years, its a great offer.
General Drama
May 17th, 2010
MS=GT, In two years, SL will be nothing but a bawww fest of furrys, goreans and ageplayer pedophiles, i.e. the entire user base will be current and former staff of LL.
Ted
May 17th, 2010
I’ve mentioned all along on this site that the TPV clients were making connections to non-linden home sites, not just SL. For what ever purpose, I’ve never agreed to these connections being made without my knowledge. I’ve even wrote other client creators and asked them why the clients were contacting their sites or IP’s. I’ve also asked them to create an opt-out for any connections being made to no avail. I was never returned a response from the client devs I’ve contacted.
I don’t believe all are bad intentioned, but I do believe that what we are seeing here shouldn’t be allowed for several reasons. And at the least a privacy statement should detail what information is collected and for what purpose.
At minimum, you should always put up a local port sniffer/logger when trying a new client and see what connections are being made, if necessary block any incoming + outgoing IP via a firewall, or alter the code to remove the connections. I’ve found most clients that I’ve use do indeed make connections to the developers site.
Ted
May 17th, 2010
Just another small note. Remember that a TPV developer need not create any additional connections to their site for their client to work on the Linden grid. Nor for any purpose in reality unless they themselves are hosting the grid network. And even then would only be needed for connection purposes. Any information at all sent to a third party site should not be tolerated as a general practice as it opens up further potential security issues between the client and the server (different types of security issues at that ex: phishing).
In other words, common sense should prevail before accepting the connection, or taking for granted that the connection being made is for legitimate use or needed at all. If you monitor the Linden open client v1+, you will see that it only makes connections to the Linden grid. Any code alterations from Linden’s client source code that alter this fact should be circumspect and further looked into before continuing use.
Ted
May 17th, 2010
wrote:
“It’s being retained for the purpose of getting an SL user’s RL data arbitrarily.”
The above pretty much says it all.
1) Third party viewer’s, their sites, their work, doesn’t require, need, nor warrant any SL users information for the purpose of connecting to Second Life and should not be allowed.
2) This shows the difference between those that believe in open computing and freedom to compute, verses those that just use open code as a stage for their own purpose and desire. The information collected in no way represents any necessity nor any benefit to those that use the client. Nor does it promote open computing and the ability to freely compute as one desires. It does the opposite and creates mistrust. No matter the intention.
Just the use of the word “data mining” should be a clear statement of intent, as well as a huge embarrassment to the Emerald client and it’s developers if indeed the facts on this site are accurate.
While Internet Protocol, avatar UUID, and collected information as viewed may not be associated with personal private information, it’s intent is indeed to provide such developers with personal identification. None of which is required or needed for the operation of the client in conjunction with the Linden grid.
Emerald Dev’s Modular Systems Data Mine Tracks 16,740 Avatars | The Alphaville Herald
May 17th, 2010
[...] recently leaked from the ModularSystems.com web site include a dump of a secret “datamine” data base [...]
Jayd3n
May 18th, 2010
Linden Lab Shut down woodbury because of onyx/emerald.
Why Doesnt Emerald get Banned, their Sims taken just as woodbury was, are these guys allowed to do such, and copybot other users, as well as grief, and use CDS, and Emerald to Datamine without concent : O?
Why not shut them down as well, the Stupid onyx project, and CDS and any other systems like it need to go. Emerald is BAD for the community.
Babsy M.
May 18th, 2010
leaked copies of onyx svn all over thepiratebay & isohunt.. R.I.P emerald viewer
Did Linden Lab’s Emerald Dev Coverup Lead To Woodbury Ban? | The Alphaville Herald
May 19th, 2010
[...] attempted coverup of the leaked ModularSystems.com datamine database connecting IP addresses and Second Life avatars names may have been to blame for Linden Lab’s [...]
Reso pubblico un database di dati personali raccolti dal team di Emerald. Prime considerazioni « Opensource Obscure
May 20th, 2010
[...] Lab potrebbe pensarla diversamente. Se lo scambio di email pubblicato dall’Alphaville Herald è autentico, Soft Linden aveva scritto al riguardo in uno [...]
Psyke Phaeton
May 21st, 2010
If you want to vote for constructive changes to the official client to help with managing our privacy please click http://psykephaeton.net/mediaprivacy
King Reggin
May 31st, 2010
Get a first life. Maybe you’ll learn to get one now that all your IPs have been mined and you’ll get hacked by some kiddy.
LordGregGreg Exits Emerald Viewer Team | The Alphaville Herald
Aug 15th, 2010
[...] But drama has plagued the group – most recently the Emerald developers have been at the center of a series of revelations that the Emerald viewer harvests the directory path from which the application is run and stores this in the baked avatar texture, where it can be retrieved by others. With some users running Emerald from their home directory, usernames and real life full names can be exposed via the avatar texture. While the directory path is encrypted, the encryption has been broken on two occasions to date. [...]